Microsoft's Active Directory (AD) provides centralised identification and authentication services to Windows networks.
In recent years, as more applications have been integrated under the AD umbrella, it has become a central repository used by organisations to manage users identities and access rights. As a result, it has become a trove of sensitive information and in turn a prime target for hackers.
The network's sensitive spot
Until not so very long ago, organisations expected threats to come from the outside of the IT infrastructure. Consequently, they did not pay particular attention to securing the AD since they considered it was located inside a safe zone. Of course, organisations have since revised their assessment of risk. It is wise for them to “assume breach” and consider what an attacker might do if he already has a foothold on an internal system.
As far as internal threats go, it can be assumed that any hacker will go straight for the Active Directory if he can.
Hitting where it hurts
When considering AD security, here are in our opinion the 3 main risk scenarios:
1. Group security
Active Directory groups make it possible to manage user rights, from basic to privileged. The more privileged the group is the more valuable target it will be for a hacker. Example: the Domain Admin group, which allows its members full rights on the whole domain. Other groups are used to manage access to critical applications (such as SAP and Unix servers) and can also prove very interesting for hackers. It is therefore necessary to make sure that such groups are no bigger than strictly necessary and that users are carefully vetted. Any change in the group's users or structure should be validated.
There are two different ways of handling this, and neither is easy:
- The restrictive approach : manual validation is required from management to add a user to a sensitive group
- The reactive approach: changes are monitored automatically and any anomaly will trigger an alert (we'll come back to that).
2. Group policy objects (GPO)
Group policy provides centralised management and operating systems configuration for an organisation's computing environment. This is a powerful IT management tool, but it can potentially also enable a hacker to spread malware and compromise a whole network if he manages to modify a policy.
As above, a restrictive or a reactive approach can be used to validate changes in group policy objects.
3. Passwords and privileges
Passwords and privileges are managed by the Active Directory. Security can be improved by enforcing stronger passwords (long, complex, impersonal, unique, secret...) but due to the way Windows works, this isn't sufficient. When using an account, a Windows user leaves traces. These traces make it possible for a hacker, if inside the network, to target that user's account and potentially obtain its credentials.
To reduce its exposure to risk, a privileged account should not be used on a constant basis. Therefore, the only real way to achieve strong security is to use dedicated accounts: one standard account meant to be used for daily activities and one or multiple admin accounts for non-standard actions. Access rights for the standard account must be defined carefully and be both protective enough and comprehensive enough to allow for common requirements without having to revert constantly to a higher level of permission.
Tackling AD Protection
Restricting changes is not today considered the best approach to keep the Active Directory secure. The current trend is rather to "let the AD live" and monitor it dynamically, based on intelligent risk-evaluation algorithms. These algorithms will analyse any changes in the AD and an alert will be triggered in case of anomaly.
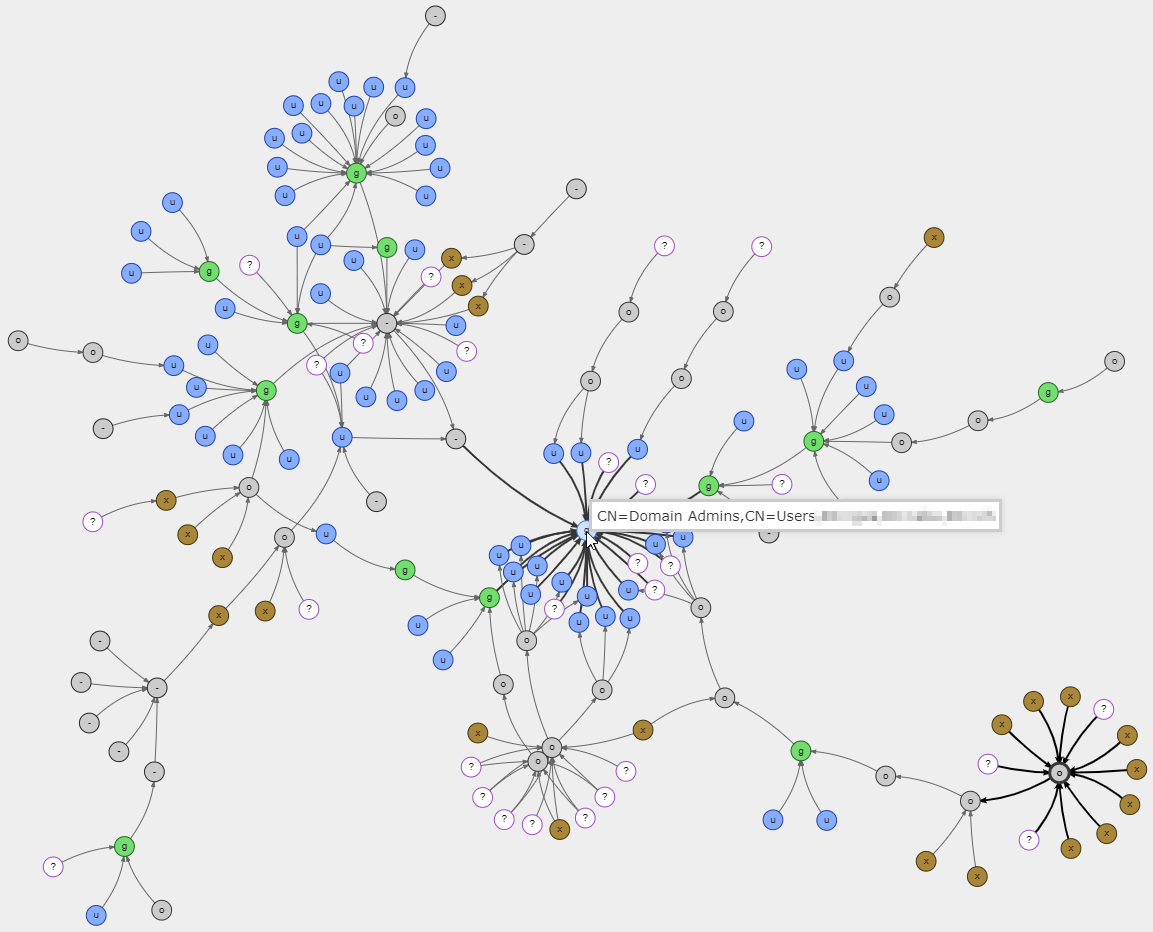
Besides, and importantly: AD security should not be viewed only through the eyes of the defender but also from the perspective of the hacker. Here is an example: once the organisation has validated an admin group's security in the AD, the process does not end there. There may be sub-groups, delegations, GPO startup and login scripts, - which are not easily visible to the defender but will benefit from the same access rights. The defender might not necessarily check all links and the attacker will definitely find the weakest, unknown ones. In view of this, defenders should stop thinking in terms of "bullet points" and rather work on checking dependency graphs, mimicking the attackers’ thinking.
The following sample graph, built by a customer using an open source tool, shows a real environment and the sheer number of both direct and indirect paths from AD objects to the critical “Domain Administrators” group.
Open source vs commercial solutions
Today, open source tools such as Ping Castle and BloodHound can digest a large quantity of data and are very good at providing a snapshot of the current AD dependencies.
On the other hand, commercial tools are required in order to provide continuous monitoring over time and assess the impact of changes to the overall security posture of the entire Active Directory.
Full disclosure: Navixia works with both types of tools. With open source tools for punctual security assessments. With ALSID, a commercial solution that provides a continuous monitoring of Active Directory security, for an efficient daily protection.