The world of internet fraud (or “scams” in computer jargon) is growing at an astounding rate. Of course, there is always Mr. Mamatou, living in Central Africa, who wants to leave you some of his inheritance in his will. In theory, putting down a deposit to pay for the banking fees in order to receive several million in your bank account should do the trick. Apart from a few unsuspecting victims, people quickly realise that it is a con. However, other types of fraud are far more treacherous.
New ways of scamming
The new type of fraud found on the internet today is more sophisticated and specifically targeted. It is therefore more difficult to detect. With relatively little means, but used in a cunning way, scammers can easily con money out of innocent internet users. By chance, we stumbled upon one such scam through an advert for a camera found on a Swiss site for online classifieds. Technically dissecting the inner workings of this scam allows us to make some interesting discoveries and to shed light on a tried and tested system active throughout Europe.
Scam summary
It all starts with an advert for a camera on a well-known Swiss classifieds site. The offer, though good value for money, seems real. Several e-mails are exchanged with the vendor, a certain Rebecca, without the slightest mention of money. The exchanges are predominantly technical questions. Rebecca explains that she now lives in London but previously lived in Basel and, because of this, the warranty was taken out in Switzerland which is where she is looking to sell the camera.
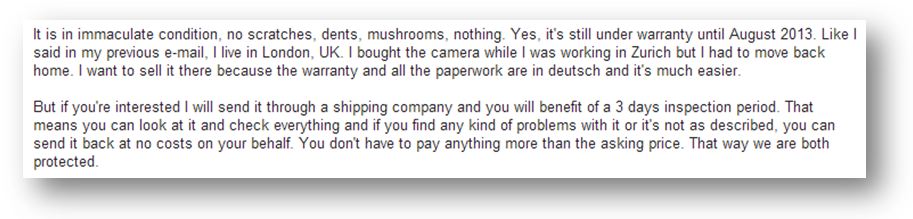
Rebecca then proposes to send the package to us, at her own cost, through an intermediary shipping company similar to DHL. We will have 3 days to inspect the product and if we are not satisfied, we can send it back to her.
Email exchange
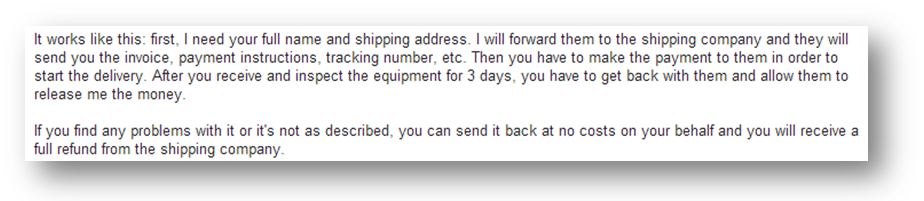
In the following mail, the process is changed slightly, as now it is necessary to pay the full price of the camera and the money stays blocked in the shipping company's account. If we decide to keep the package after the 3 days, the shipping company then transfers the money to Rebecca.
Rebecca also sends a copy of her passport to confirm her identity.

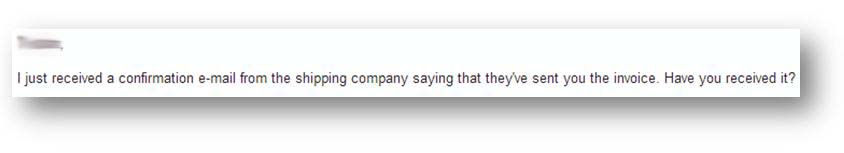
After giving the address to Rebecca, we quickly receive an e-mail from her stating that she has sent the product to the shipping company and they should be in contact soon.
The role of the “shipping company”
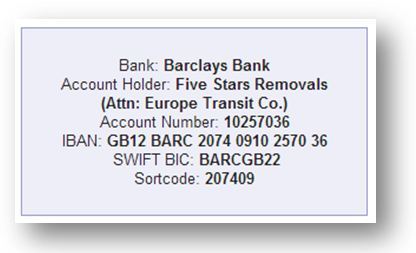
The same day, we receive an e-mail from europe-transit.com stating that a package is being held at their warehouse. The payment is to be deposited into their Barclays Bank account. The e-mail also provides a tracking number in order to trace the package.
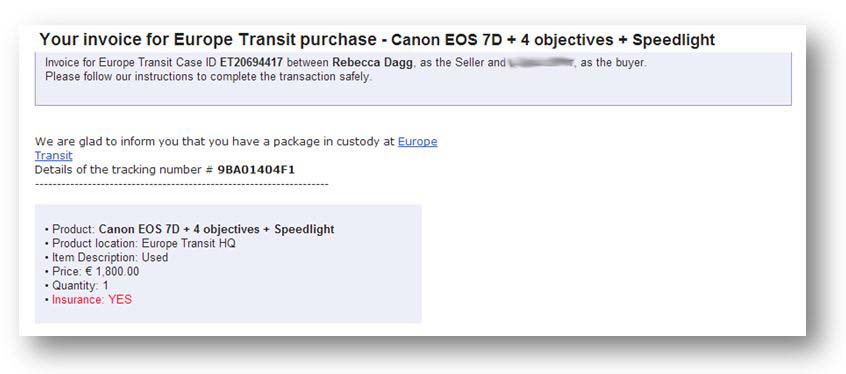
On the shipping company's website, there is a page allowing us to track our parcel.
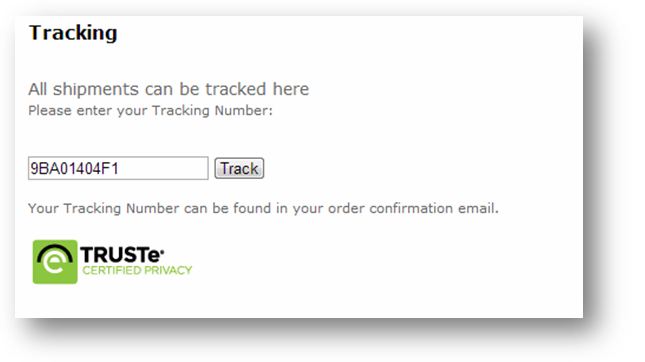
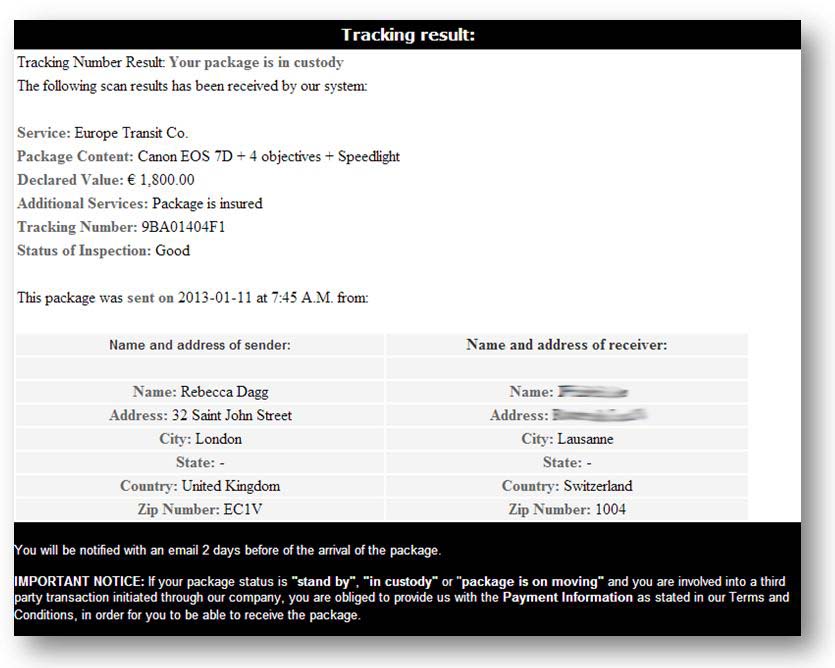
Everything seems in order, the only thing left to do is make the payment...
Behind the scenes
We start by researching Rebecca Dagg. The first results are particularly revealing as they all point to a scam. Clearly this is not Rebecca's first time! We also find other passports under her name but with different photos. If we were choosing, we would have used this one rather than the first one!

Although the procedure seems to be the real thing since the shipping company guarantees the transaction, we decide to do some more checks. Why not meet Rebecca in London next week?
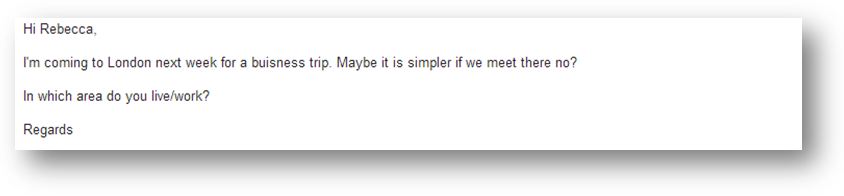
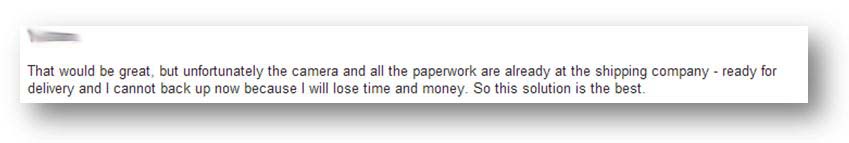
Well, we tried…
Fake shipping company sites
Now onto the shipping company website, europe-transit.com. The source code of the welcome page reveals an interesting comment.
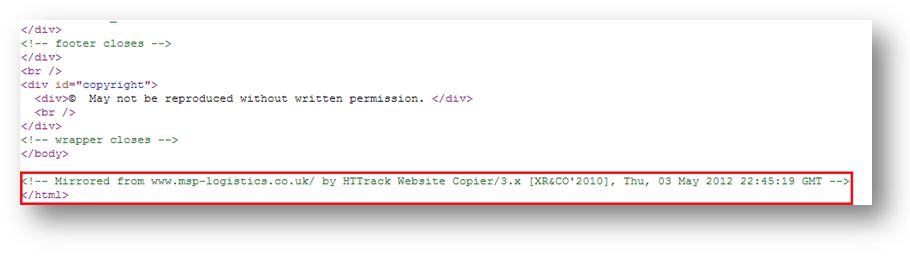
The site was copied using software which, in the process, added its own signature. The name of the copied source site also appears. The original differs very little from europe-transit.com as only the contact form has been replaced by the parcel tracking system. MSP is also a logistics company, transporting throughout Europe, and this choice is not insignificant as it can easily mislead people who are familiar with the original company.

The scammers' techniques
By meticulously analysing the site, we come across several hidden pages as well as a password-protected administrator user interface. The first page allows the scammers to create entries for new clients/victims. Following this, an e-mail is sent to the victim, informing them that a package is being held by the shipping company. The victim can then check for themselves that the company exists and that a parcel has been registered in their name.
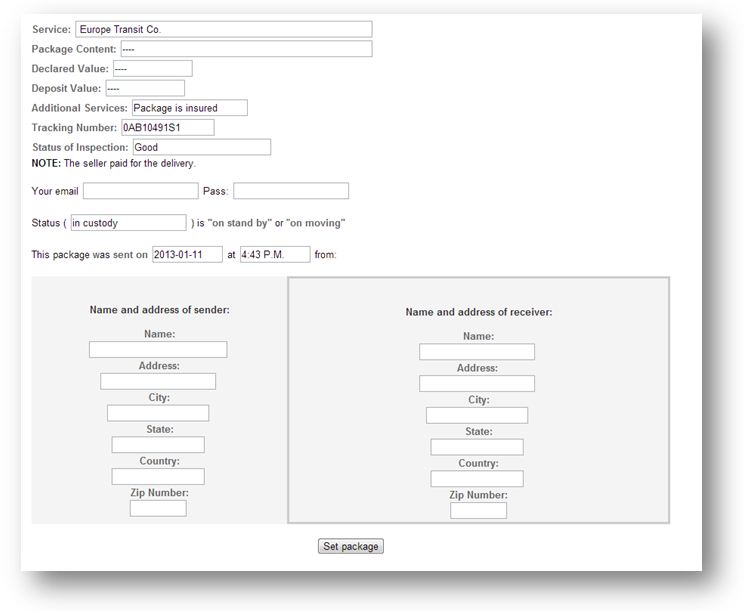
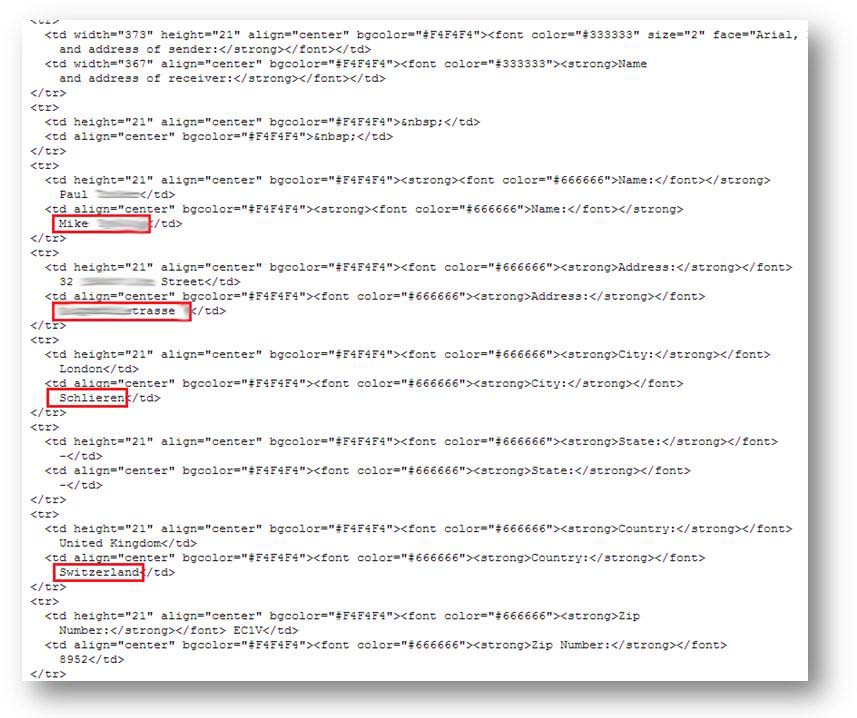
We also find a file listing the information for all the fake parcels. Rather than using a database, the system generates an XML file for every new victim.

Gathering the information
Each one of these files contains the details entered in the form above: name, surname, address, package content, etc.
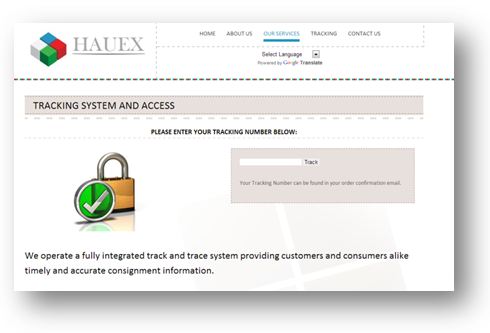
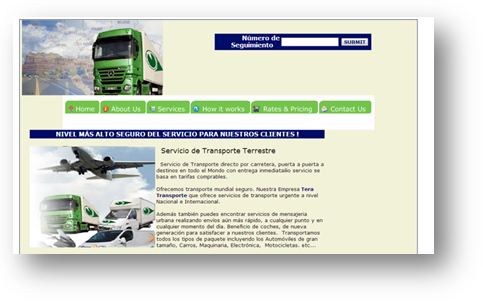
Other similar sites
When searching the web, we quickly found five other sites similar to europe-transit.com. They also hosted a fake parcel tracking system :
- http:// newrosslogistics.com/track.html
- http:// hauex.com
- http:// www.teratransporte.com/es/
- http:// speedinter.co.uk
- http:// straight-freight.com/es
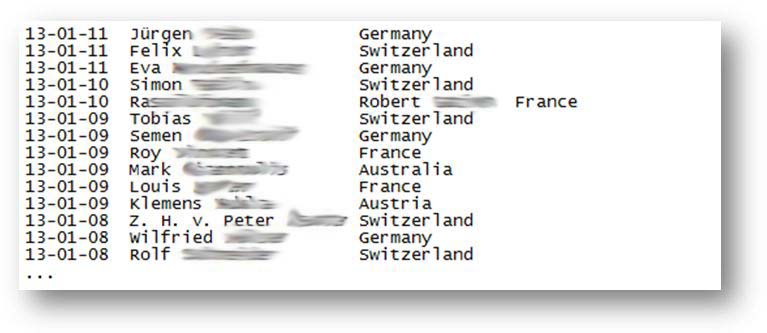
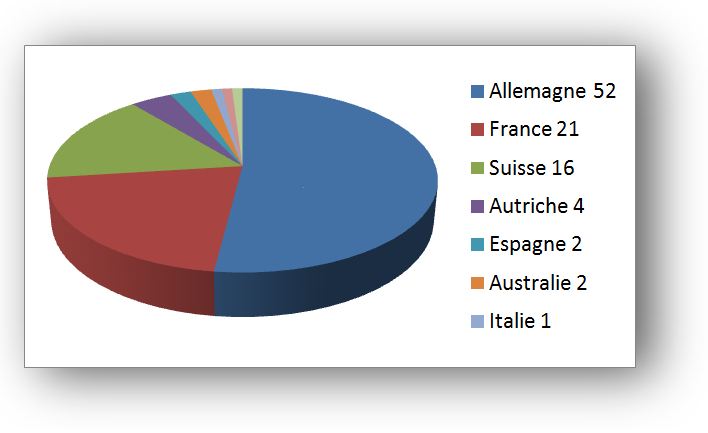
Some statistics
We extracted the following statistics using the files present on the different sites. The oldest site dates from 8th November 2012 which suggests that this scam has been in place since this date, or that older files are regularly deleted. In total we found files containing information for around 800 victims. More than 50% of the victims are in Germany, 21% in France and 16% in Switzerland.
Where is Rebecca?
The final stage consists of trying to identify the person behind the scam: Rebecca. In order to do this we used an XSS flaw present in the form used to create a new package. Once in place, we sent another e-mail to Rebecca in order to make her visit the page in question.
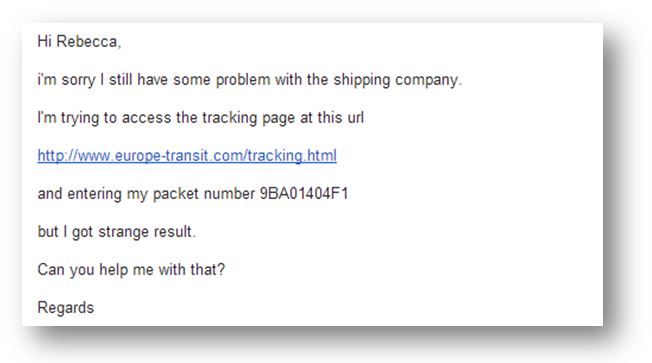
The injected script was executed when Rebecca accessed this page. This allowed us to get her IP address as well as her cookies for europe-transit.com. These could have been used to access the authenticated part of the site. “Could have”, because unfortunately these cookies had been configured with the flag “httpOnly” which restricts their use and does not allow scripts to access them. It should be noted that this flag, whose importance is often underestimated, is rarely present in the various assessments which we carry out.
We were however able to acquire Rebecca's IP address, which could be geolocated in England.
Further investigation showed that the IP address belonged to a company computer which had clearly been compromised by the scammers.
Conclusion
Our investigation ends there. It highlights the workings of an increasingly present form of fraud which can ensnare not only the buyer of the proposed “products” but also the companies whose IT infrastructure is insufficiently protected and can therefore be exploited by the people behind these scams.
