It may look obvious, and yet ... We carry out the so-called "click tests" regularly as part of the security assessments we perform for our customers. They aim to find out if company employees can resist clicking when they receive an email containing a tempting or intriguing URL.
Will they click ? Will they provide their credentials or the personal information required ? Or will they, as hoped, detect the phishing attempts and discard the malicious email ?
Just as any other security assessment, this test is performed in close collaboration with the management team.
Step 1: Get valid email addresses
As an email address repository, the internet proves to be a goldmine. We already mentioned in a prior blog post that an incredible amount of information sits within easy reach on the internet. Social networks are particularly useful to hackers, since users continuously feed their profiles with a tremendous lot of personal information.
To demonstrate how easily information can be gathered, here is an example based on Navixia. Our homemade research tool visited the internet - including a selection of social networks - looking for personal profiles associated with our company. It then deduced (successfully) the names of our employees.
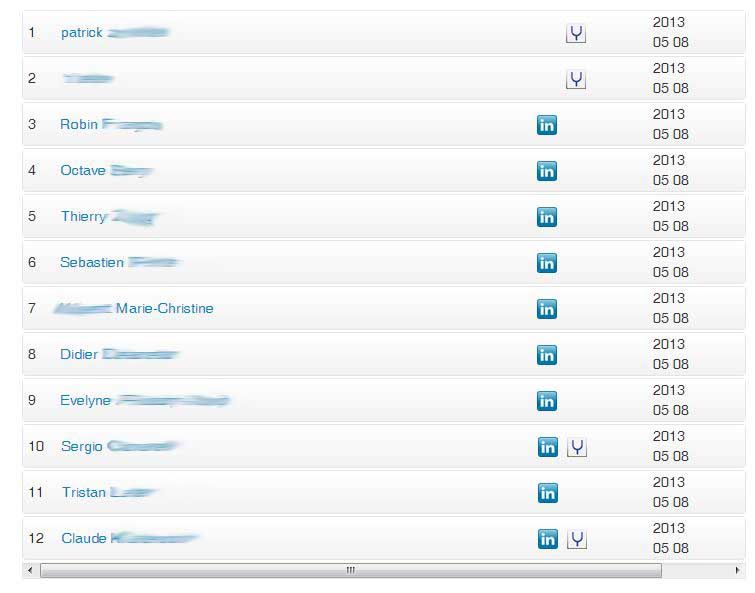
Our tool then tried (again successfully) to reconstruct and validate our employees' e-mail addresses, using various potential syntaxes.
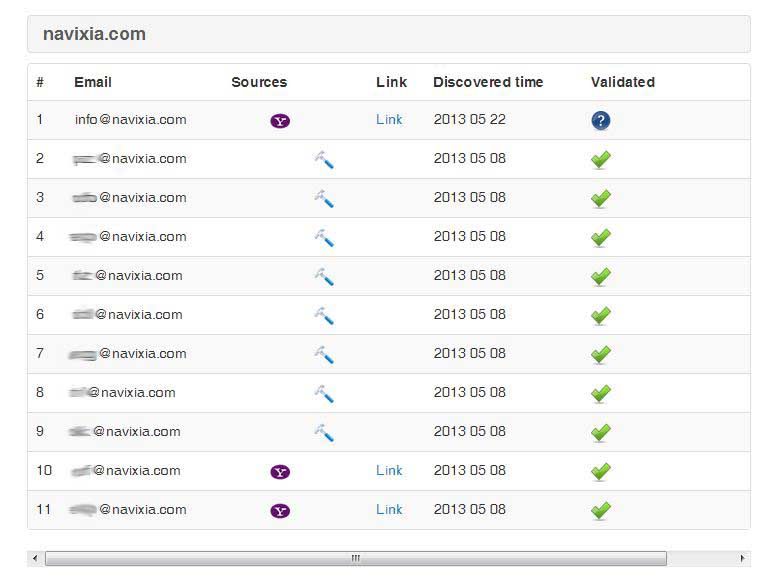
When we perform a click test, and depending on the kind of assessment required, our customers may also want to provide us with a pre-defined list of email addresses to test. In that case, we wouldn't need to perform the above search.
Step Two: Sending phishing emails
This is where we send an email message to all employees for whom we have an email address. The message is meant to be either tempting or intriguing, in order to induce the recipients to click. The idea is to see how they react - if they click (or not) on the link provided. The results are interesting.
For "savvy" users, whose company has trained them actively to recognise phishing, the click test will have a very low success rate (1% to 4%). Sometimes, users even report the phishing attempt to their IT department.
On the other hand, users who lack a proper awareness training do not fare so well. In that case, the potential success rate of a phishing campaign is much higher. From experience, we can anticipate that 12% to 18% (!) of users will click on the links they received and provide the requested information. In other words, even in security-aware Switzerland, one or two users out of ten are likely to "invite" intruders into the network if their company has not trained them adequately beforehand. Food for thought.
In short...
Some particularly sophisticated (and successful) phishing attacks reported in the news lately demonstrate the hackers' determination to make the most of such a promising approach. It is quite easy to find personal information on the internet, which allows for a very precise targeting of potential victims. Well-targeted phishing can allow an attacker to eventually access the whole corporate IT infrastructure.
Protective measures must therefore be taken beforehand. The attacker must be prevented from entering the network by all possible means. Awareness, prevention, assessments are all effective tools. They are worth using.
