Did you know it ? The "Private" tag, which can be applied to private appointments in the Outlook calendar, does not prevent a colleague to access their contents, as long as you gave them viewing rights on your calendar (a not uncommon situation in a team or department). This fact is documented by Microsoft and is not a vulnerability.
The "Private" flag is meant to be read and interpreted by Outlook to hide information. But a third party client or an Outlook plugin can be configured / developed do ignore that flag. As a result, this will enable a third party to see all details of any appointment you tagged as "private". This article will show you how this can happen.
Introduction
Navixia, as a security specialist company, is called upon to monitor the safety level of various technologies and software that are frequently used in the business world. As a result, we sometimes have to delve deeper into the way they work.
Microsoft's email application, Outlook, and its server counterpart, Exchange, are major tools in many enterprise networks.
These tools provide employees with several ways to separate their professional data from their private content.
As far as emails are concerned, employees are often advised to clearly indicate that a message is private by storing it in a "private/personal" folder, or by adding a "[Private/Personal]" tag in the email's title.
When used professionally, Outlook calendars are often shared with at least part of the company, such as a team or a department. Microsoft Outlook provides a simple way for users to enter private appointments alongside professional ones. A clickable button makes it possible to tag private appointments as "private" and so hide them from other employees.
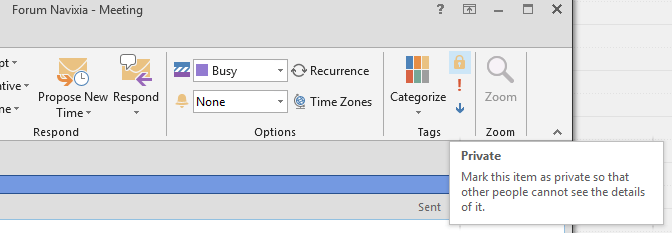
At first glance, this approach looks effective and Microsoft seems to be providing an appropriate technical answer to an existing problem. However, this does not sustain a closer examination:
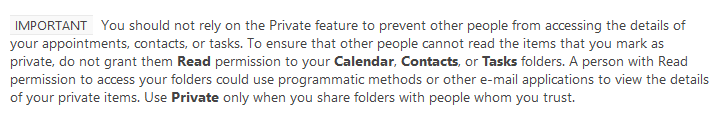
Source: Make an appointment or meeting private
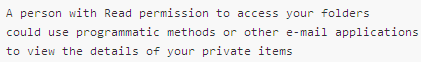
This remark, that appears clearly in Microsoft's Outlook documentation, says it all : marking an appointment as private will not hide the information from someone who has reading rights on your calendar, which is often the case within a team or department.
We wanted to check the impact of this situation and evaluate the related risk for our customers, so we decided to investigate further.
Analysis
Outlook is the Microsoft client that communicates with Exchange servers. To exchange information, both systems use:
- MAPI/RPC: Proprietary protocol developed by Microsoft for Outlook/Exchange communications.
- Exchange WebService (EWS)): Open protocol based on SOAP (XML web API) and introduced with Exchange Server 2007.
Let's now look into the EWS protocol in more details.
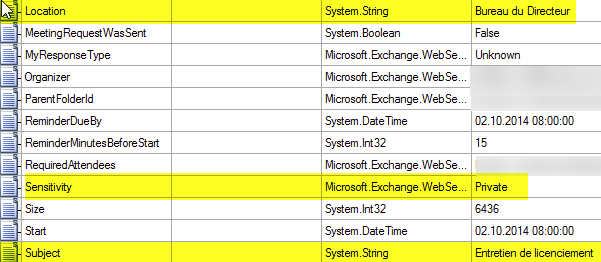
When an EWS client requests the list of appointments from a specific calendar, the Exchange server provides a list of objects. These objects are called AppointmentItem and have many parameters, among which the "Sensitivity" flag, which can have 4 different values:
- Normal
- Personal
- Private
- Confidential
This Sensitivity flag is converted to Private when the user indicates that the appointment is private.
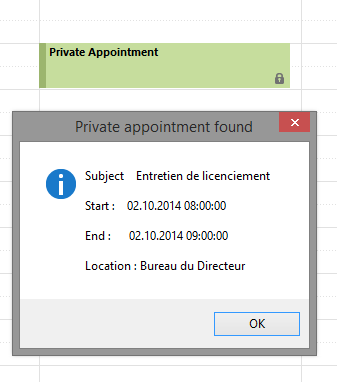
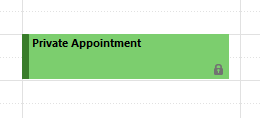
When Outlook receives an appointment whose Sensitivity flag is marked as Private, it will mask the appointment's details and show it as private, as below:
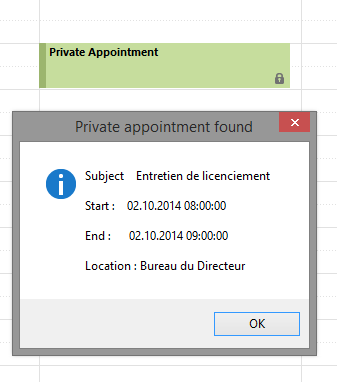
However, any other client using the EWS protocol can ignore the Sensitivity parameter and will as a result be able to read all the details that Exchange provides about the appointment.
To check this, we have developed a small Outlook plugin called UnPrivate. It can request information from the Exchange server and publish details that Outlook would hide.
Conclusion
Microsoft never concealed the fact that the "private appointments" function was an easy-to-bypass protection.
What should this teach us ?
We should always keep in mind that the technologies we use in our everyday activities do not necessarily protect our private data as well as we think. We should try to learn as much as possible about the tools we trust with our sensitive data - and at all times, we should remain cautious.
