This article describes in detail a cross site scripting (XSS) vulnerability and a cookies vulnerability found in Jahia by the Navixia Research Team. Jahia describe their solution as "the leading Java-based open source content platform for the enterprise, offering content management, collaboration, and social out-of-the-box."
The vulnerabilities have been reported to the Jahia publisher and two CVEs have been attached with the following references: CVE-2013-3920 for the XSS vulnerability and CVE-2013-4617 for the cookie vulnerability.
Summary
This article presents vulnerabilities found in the Jahia web application. Validation has been done on version 6.6.1 but the vulnerabilities were present in the older versions as well. A patch has been released and is included in the version 6.6.2. Together, the two vulnerabilities can allow an attacker to impersonate other users and their sessions.
XSS
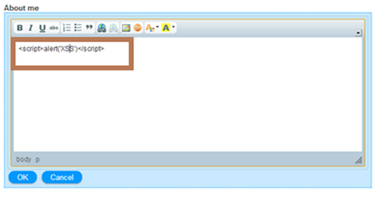
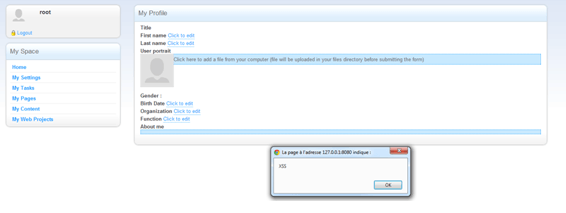
Any authenticated user is allowed to modify his profile under the tab “My Settings”. He can edit several fields like “name”, “phone”, “Facebook account” or “about me”. Most of them are filtered against XSS when posting the data to the server. The server also filters back the data when it sends info about current user or other profiles. The field “about me” is the one exception. The sanitization is done by the browser but it is possible to craft directly the request with an XSS. When the server sends the value for this field, no sanitization is performed and the XSS is triggered.
In the two following pictures we can see that when trying to write an XSS directly in the field, it will be modified and characters like < or > will be html-encoded.
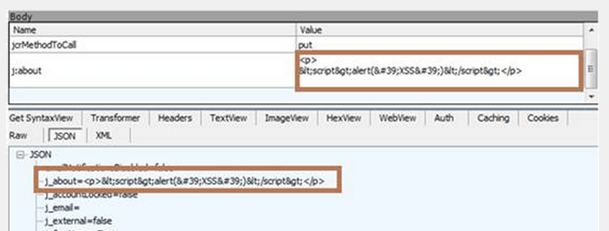
But if the the request gets modified directly, nothing is sanitized and we get the following result:
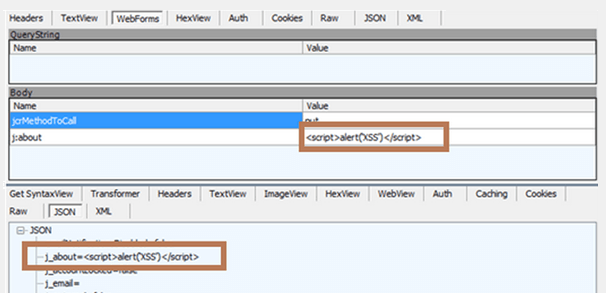
When we try to load the user profile’s page again, the XSS is triggered.
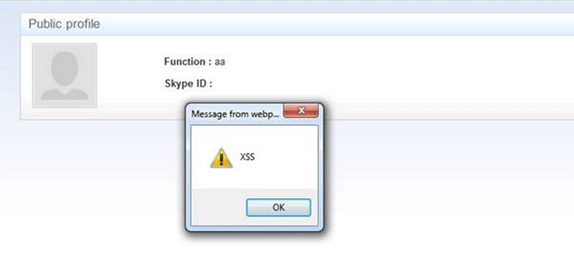
The value stored in the field « about me » is used at different places in the application, such as for example user information in the “friends” or “author” page. If an authenticated user whose "about me" field has been contaminated with malicious content browses one of these pages, a XSS will be triggered.
Cookie without HTTPOnly
Furthermore, the JSESSIONID cookie is not 'http only' by default. This means that, if used in conjunction with the previous vulnerabilities, an attacker could use this XSS to steal the session cookie of a user and impersonate him.
Navixia identified these vulnerabilities in June 2013 and they have since then been corrected by Jahia in version 6.6.2 and further.
